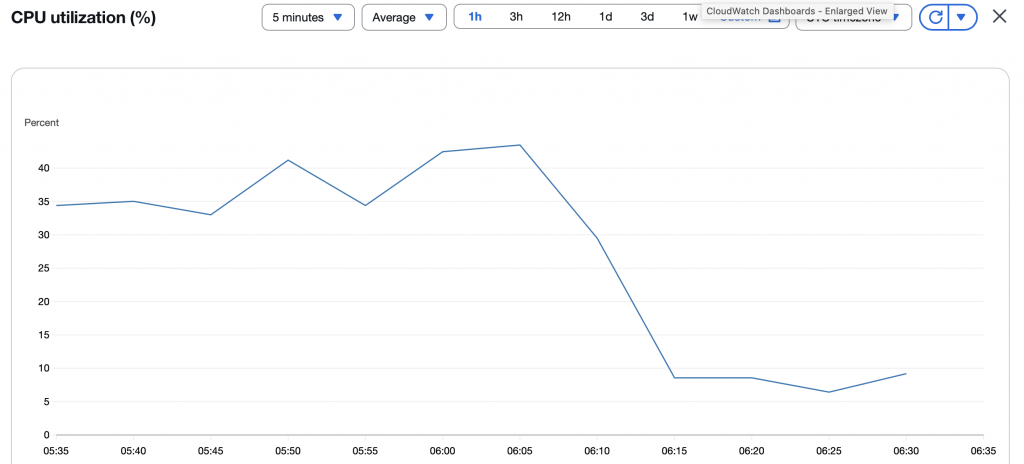
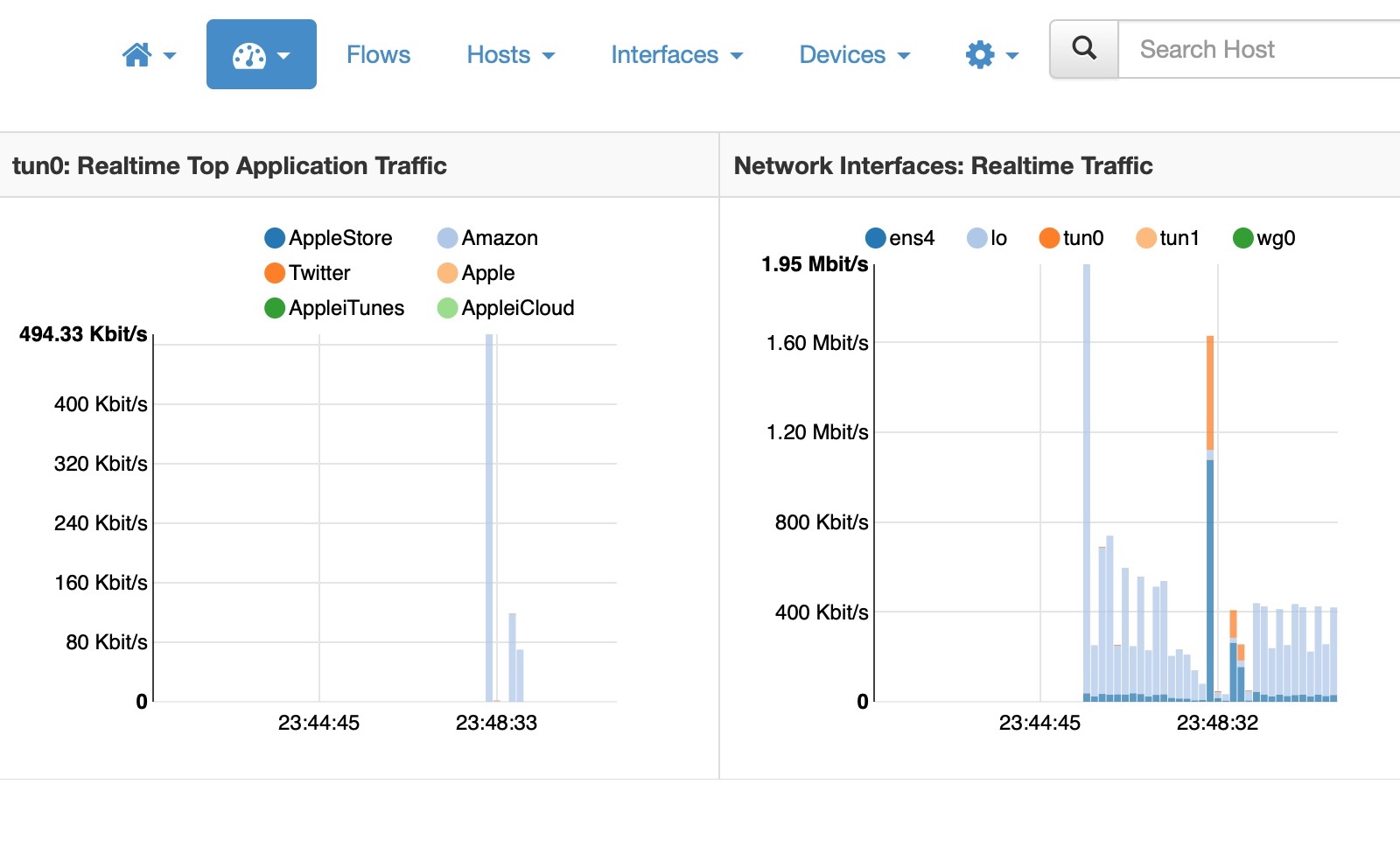
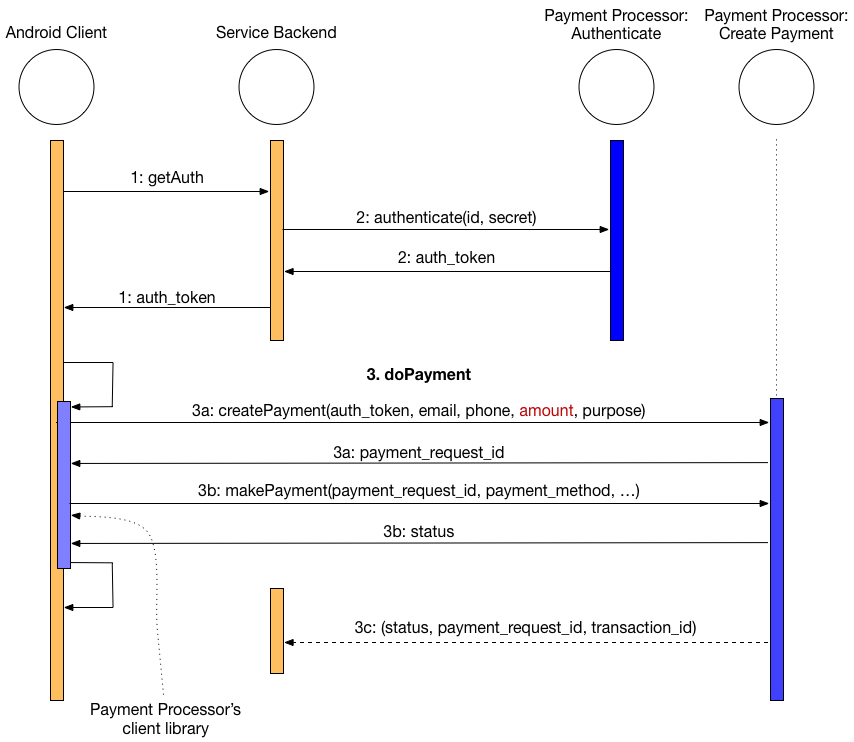
I work with a small NGO that provides an essential service to citizens. In the past year, bot traffic has overwhelmed their infrastructure, growing from a nuisance to an operational challenge. Many other SaaS and SME websites face the same issue. Bot traffic mushroomed to exceed 50% of all web traffic in 2024, according to […]