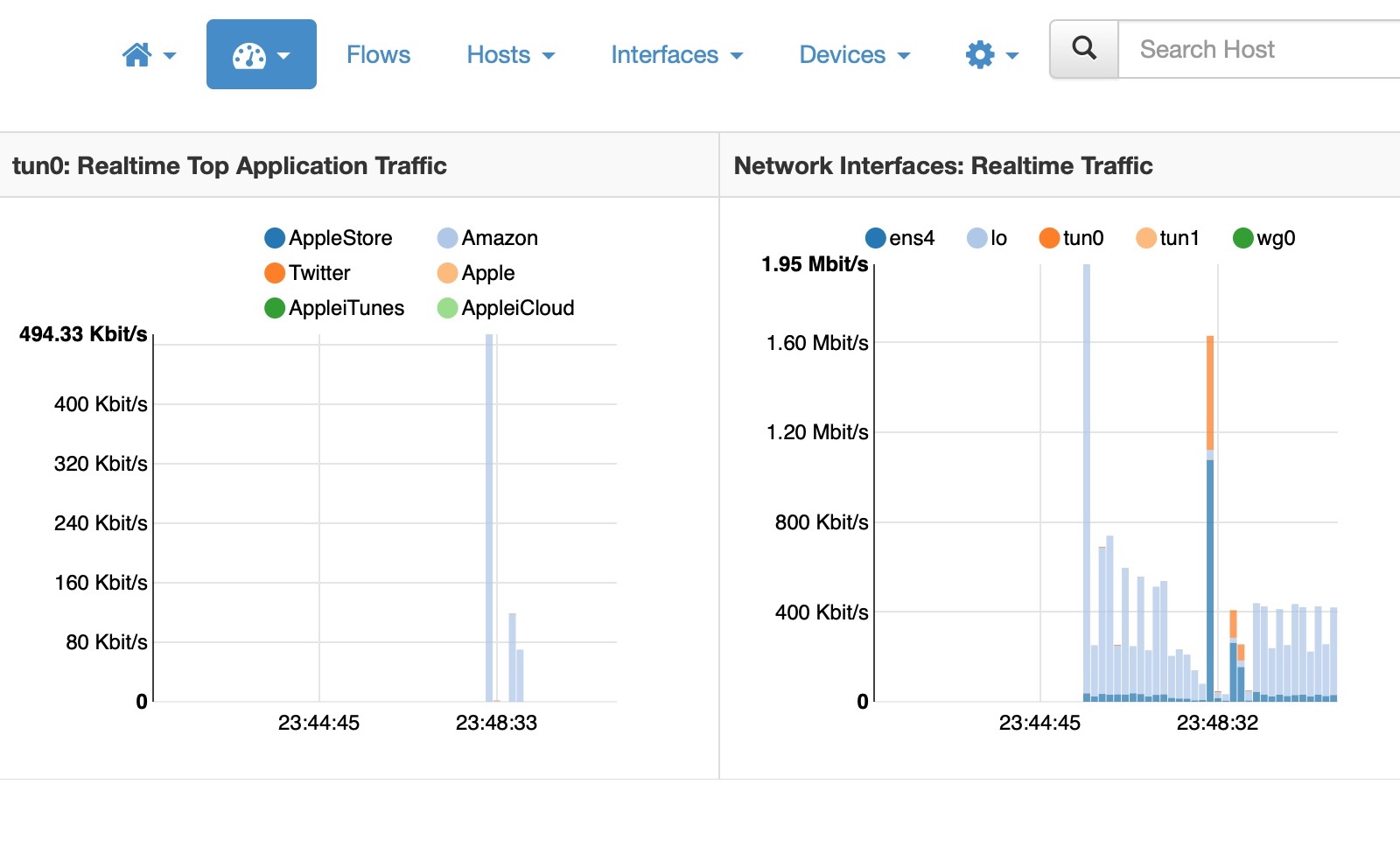
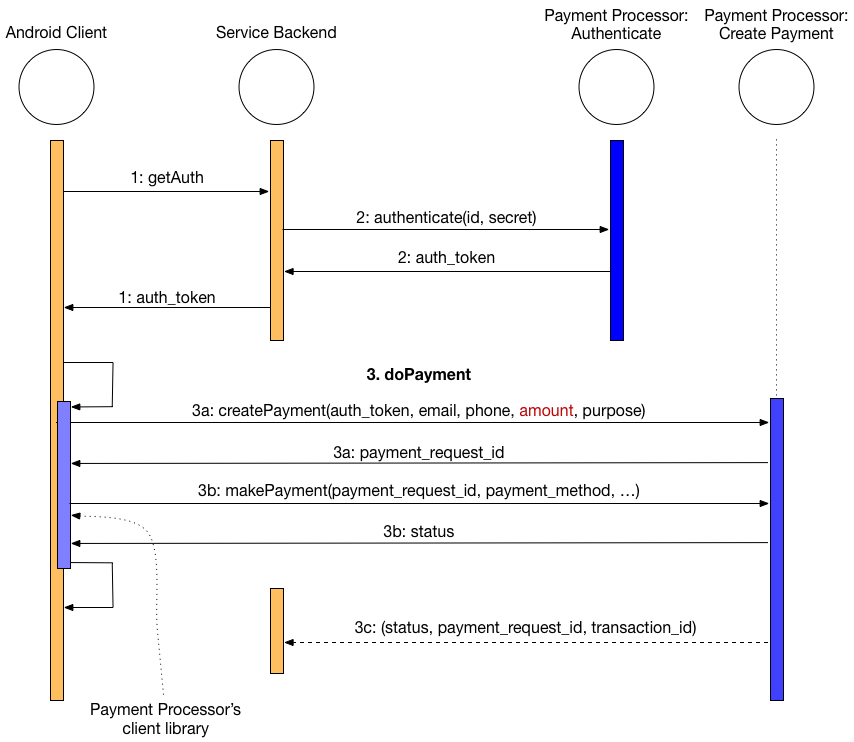
Now that we have a process that automatically builds a container image whenever changes are committed to the git repository, we need a way to get those changes out, either into a development or test environment, or to the production environment. In the gitops world, a deployment is also initiated by a change to the […]